Google OAuth 2.0
Summary
Authorize app to access a user's Google resources.
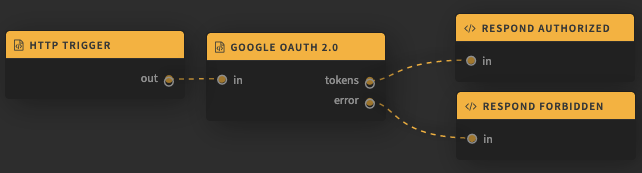
Ports
When an event is received on the in port, the user is redirected to authorize the app to access the scopes specified in Settings -> Parameters. Once authorized, the received event, with tokens attatched, is routed to tokens.
If the user denies the application access, or tokens cannot be retrived, the event with details about the error is routed to error.
Input/Output Format
Any object may be routed to the in port.
The received event is routed as is to both output ports with the following modifications:
Events routed to tokens has the property tokens set to an object. That object has the following form:
{
access_token,
expires_in,
refresh_token,
scope,
token_type,
id_token,
}access_token: string Token used to authenticate against Google APIs.
expires_in: number Seconds the token is valid for.
refresh_token: string|undefined Token to obtain new access tokens. Not present if user already has authorized app.
scope: string Space-delimited list of scopes granted by the access token.
token_type: string always Bearer.
id_token: string JWT with information about the user. Validatate in accordance with Google's documentation. Only present if the scope openid is requested.
Events routed to the port fail has the property err set with a value that describes the error that occured.
Events
This functions emits responses that redirect the client to Google's OAuth endpoint. The client is redirected back to app and specifically this function. Once an event is routed to an output port, this function listens for events named response.
As one HTTP request is replaced with another, using the functions ought to be a transparent experience.
Other
If the user does not complete the an authorization attempt in 30 mins, the user is considered to have abandoned the attempt. In such case, no event is routed to any output port.
Security
The tokens attatched to the event should be handled carefully. They are credentials that are tied to the app. Anyone that gain access to the tokens may impersonate the app.
Therefore, be mindful to NEVER leak the tokens, in logs, in response bodies or otherwise. ALWAYS store tokens in secure containers.
Updated 4 months ago
